Worldwide of computerized interaction, private online messaging is taking around. Folks use it for personalized, function, and company conversation. The benefit, pace, and privacy of individual text messaging websites cause them to a crucial part of our own day-to-day interaction. Nonetheless, with all the go up of those platforms comes a brand new list of problems. One of these difficulties is definitely the stability of private data and interaction in exclusive messages. Within this post, we’ll explore several of the techniques invisible in private message and how they can be discovered.
Misunderstood messages – Personal messages are prone to misinterpretation, particularly if an individual isn’t informed about the sender’s strengthen or perspective. A basic concept can be easily misunderstood, causing frustration and in many cases destroying connections. It’s crucial to be cautious with our information, making certain they are clear, to the point, and comprehensible. In order to avoid misunderstandings, make an effort to involve contextual information inside your information. Look at the conversation historical past, the strengthen of your information, along with the recipient’s reply. If uncertain, it’s best to clarify whatever you imply and steer clear of ambiguity.
Key vocabulary – One of the ways people maintain personal privacy inside their online messaging is the use of magic formula different languages. Concealed connotations and coded phrases enables you to convey information to some picked market while keeping it key from other individuals. As an example, men and women may use acronyms and abbreviations, for example LOL or BTW, and emojis to communicate a message within a invisible terminology. This could make comprehending the information demanding, plus an outsider might skip the secret information. However, top secret spoken languages can even be misused in cyber criminal offenses and harassment. Cybercriminals use invisible words to organize illegal pursuits or give destructive emails.
Deleted communications – Several online messaging programs now enable users to remove a note they’ve delivered to a person privately. This feature is a useful resource that will help users tidy up their chats and get away from faults. However, it may be a struggle for investigators who need use of communications for lawful good reasons. Even though the communications are removed from the sender’s and recipient’s chat history, they can nonetheless be retrieved through forensic computer software. For example, data recovery software can access the cache recollection from the iphone app and retrieve the deleted information. Therefore, take care when getting rid of information, because they can certainly be reached.
Checking emails – Online messaging programs have characteristics that permit consumers to follow their messages’ progress, for example invoices, read notifications, and keying in signs. These functions could be ideal for connection, nevertheless they can also be damaging if employed maliciously. For example, checking someone’s emails without their authorization can be viewed as stalking. It’s important to respect people’s personal privacy and steer clear of making use of checking capabilities without their permission.
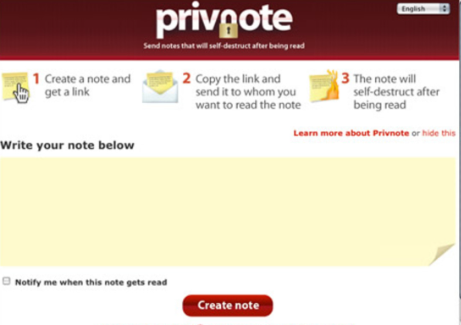
Stop-to-finish encryption – To safe privacy in online messaging, a lot of programs use finish-to-finish file encryption. This encryption makes sure that emails are only visible to the sender and the receiver of the email rather than intermediaries including the system or govt. Finish-to-end file encryption is regarded as the safe approach to interact privately because it works with a distinctive answer to encrypt and decrypt messages. Even when somebody intercepts the message, they cannot understand it without the exclusive important. For that reason, it’s vital to use systems which have stop-to-finish file encryption to safeguard your level of privacy.
To put it briefly:
Individual online messaging could be a secure and efficient approach to connect, it also incorporates its threats. However, with all the correct techniques, one could use personal text messaging tightly. To be sure the safety of the messages, be careful with what you create, avoid using secret languages that will bring you in trouble, steer clear of removing communications which might be crucial, value people’s privacy, and choose websites that have the end-to-stop file encryption feature. With those ideas, it is possible to protect your information and interaction from unwanted access, whilst still experiencing the ease of private online messaging.